How to Create Custom Active Directory Certificate Templates
Sep 9, 2025
How to Create Custom Active Directory Certificate Templates
|
OVERVIEW: This page walks you through the process of creating templates from duplicates of default templates for both User and Machine Authentication. At the completion of this procedure, you will be able to custom active directory templates. If you are looking to edit your GPO for certificate enrolment, please refer to this guide. |
Depending on the use case that you implement, you will need to duplicate one of the default Certificate templates. Duplication is not required but is strongly recommended to avoid changing the properties of default templates and to better control the changes applied to templates that work with the Certificate Automation Manager. The following table summarizes the appropriate default Certificate template that you should use to create a custom one depending on the use case:
| Use Case | Default Certificate Template |
|---|---|
| Client Authentication | User |
| Machine Authentication | Workstation Authentication |
| Secure Email (S/MIME) | User |
| Key Archival | User |
| Key Recovery Agent | Key Recovery Agent |
| CA Exchange | CA Exchange |
There are several Certificate template settings that will vary depending on the use case. The following details which settings apply to which Certificate template and use case:
| Certificate Template Tab | Certificate Template Settings | Description | Applies To |
|---|---|---|---|
| General | Template display name | This will determine the name listed when manually enrolling. | Any certificate template or use case |
| Template name | The template name will be the same as the template display name, but with spaces removed. | Any certificate template or use case | |
| Validity period | This determines the validity period requested for the certificate, same as in GCC. | Any certificate template or use case | |
| Renewal period | This is how long before the certificate expires that it can be renewed. | Any certificate template or use case | |
| Publish certificate in Active Directory | This is generally only used for User certificates and determines whether the certificate will be copied to the Active Directory User Object certificate store or not. | User certificates, use cases that apply to users, e.g. S/MIME | |
| Do not automatically reenroll if a duplicate certificate exists in Active Directory | This will prevent a user from automatically reenrolling for a certificate based on the same template when logging into another machine if the certificate had been published in Active Directory from the machine they originally enrolled on. | User certificates, use cases that apply to users, e.g. S/MIME | |
| Subject Name | Supply in the request | The Subject Name will be supplied in the certificate request. This is used when submitting a custom CSR, or when using Certificate Automation Manager Manual Enrollment Website. | Any certificate template or use case |
| Build from this Active Directory information | The Subject Name will be supplied by Active Directory | Any certificate template or use case | |
| Common Name | This will pull the users pre-Windows 2000 Logon user name. (This will be case regardless of what version of Windows they are using.) | Any certificate template or use case | |
| Fully Distinguished Name | This will retrieve the full name of a user or computer account that you see in Active Directory Users and Computers | Any certificate template or use case | |
| Include e-mail name in subject name | This will include the email address listed on the user’s general information in AD. | User certificates, use cases that apply to users, e.g. S/MIME | |
| DNS name | This is the full name of the machine (not used for users). | Machine certificates, use cases that apply to machines, e.g. Machine Authentication | |
| User Principal Name | This is the logon name in AD (Not to be confused with the pre-Windows 2000 logon). | User certificates, use cases that apply to users, e.g. S/MIME | |
| Service Principal Name | This is used when issuing a certificate used by a service. | Not used with Certificate Automation Manager | |
| Security | Group or user names | This is to list all the groups or users that the certificate template will apply to depending on the permissions | Any certificate template or use case |
| Permissions |
|
Any certificate template or use case
|
|
| Cryptography | Minimum key size | This is the minimum Private key bit length. This should never be lower than 2048, which is what we generally use as default. Some older platforms (such as Windows Server 2008 R2) may default to 1024 and will require changing. | Any certificate template or use case |
| Providers | This dictates which cryptographic provider will be used during the certificate enrollment. Use the one that is by default. | Any certificate template or use case | |
| Request Handling | Purpose | Determines whether the certificate is used for signing, encrypting, and\or smartcard logons. | Any certificate template or use case |
| Archive subject’s encryption private key | This will archive the certificate and private key so that it may be recovered later. | This is only used for user certificates, e.g. S/MIME | |
| Allow private key to be exported | Whether or not you want users to be able to export a PFX (PKCS12) of the certificate after installation. | Any certificate template or use case | |
| Renew with the same key | Enabling this will cause the request (CSR) when renewing the certificate to be based on the same private key as the expiring certificate. | Any certificate template or use case | |
| For automatic renewal of smart card certificates, use the existing key if a new key cannot be created | This will have the request default to the private key of the expiring certificate when renewing if it is unable to create a new private key on the smart card. | This is only used for user certificates, e.g. Smartcard Logon | |
| Do the following when the subject is enrolled and when the private key associated with this certificate is used | This is whether the user will be prompted to manually enter information during enrollment, or be prompted when using the certificate, or if the request will work without user intervention. Most commonly, the "Enroll subject without requiring any user input" option is used, as the subject information is generally pulled from Active Directory. | This is only used for user certificates, e.g. S/MIME | |
| Extensions | Application Policies | This refers to the Extended Key Usages (EKUs), and this will only apply if you have enabled the custom MSSL/EPKI EKUs in the Certificate Automation Manager Portal | Any certificate template or use case (EKUs are specific to use cases) |
| Basic Constraints | If you want to apply any specific constraints to the certificate template, e.g.: mark an extension as critical | Not used with Certificate Automation Manager | |
| Certificate Template Information | This will detail the certificate template information | Any certificate template or use case | |
| Issuance Policies | Describes the conditions under which a certificate is issued | Not used with Certificate Automation Manager | |
| Key Usage | This specifies the required signature and security options for a key usage extension | Any certificate template or use case, it is strongly recommended to use the default settings. |
Guidelines
This process is done on the Certificate Automation Manager server, but may also be done on the Domain Controller if it has the Certification Authority Management Tools feature installed.
|
IMPORTANT: The following example assumes that your use case is Client Authentication, hence we will work with the User Default Template. |
-
Open MMC.exe, go to File > Add\Remove Snap-In, then select Certificate Templates, click Add, then OK.
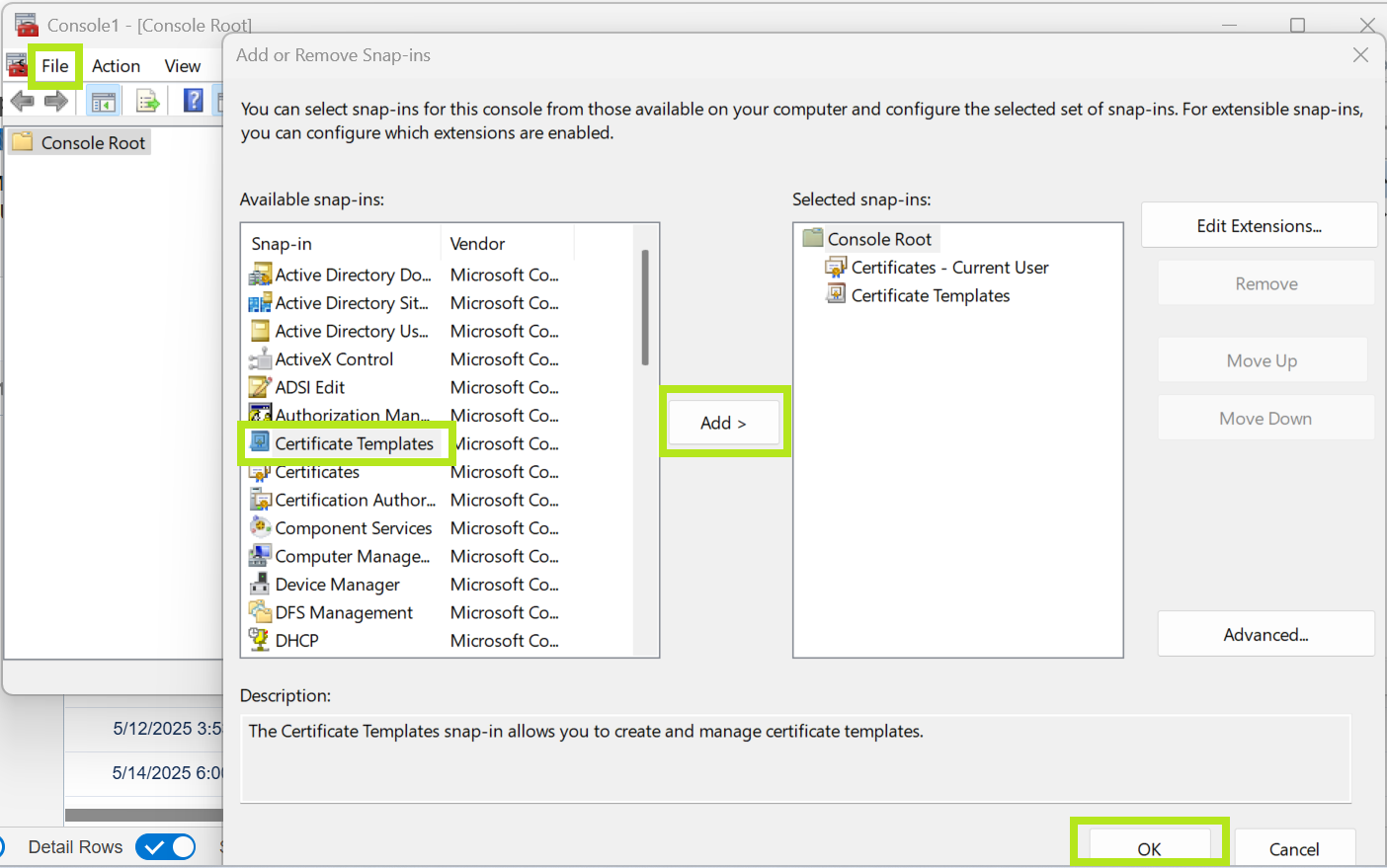
Note: When you select Certificate Templates from the navigation pane on the left, it should show you a Console with a list of templates.
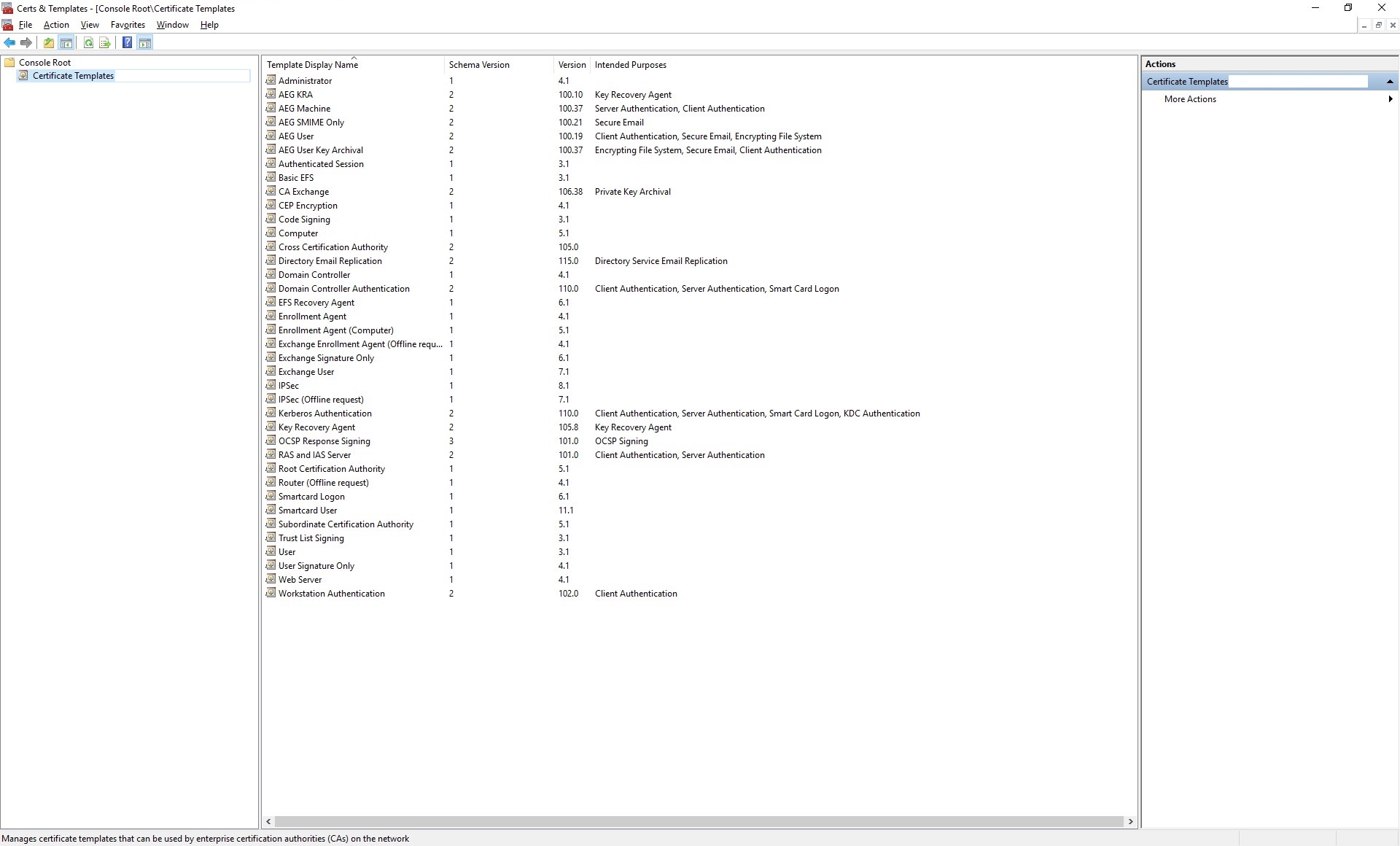
-
Select and then right-click the template you want to make a duplicate of and choose Duplicate Template.
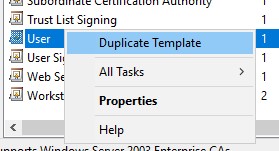
-
Go to the General tab. Enter a unique and easy to identify Template display name.
Example: If setting up a template for user Certificates that will be archived, name can be "Certificate Automation Manager User with Archival". Any naming convention should be fine.
Then, Template name will automatically be filled out with the name you provided, but without any spaces. Next, adjust the Validity period, Publish Certificate in Active Directory, and Do not automatically re-enroll... options as is needed for the use case.
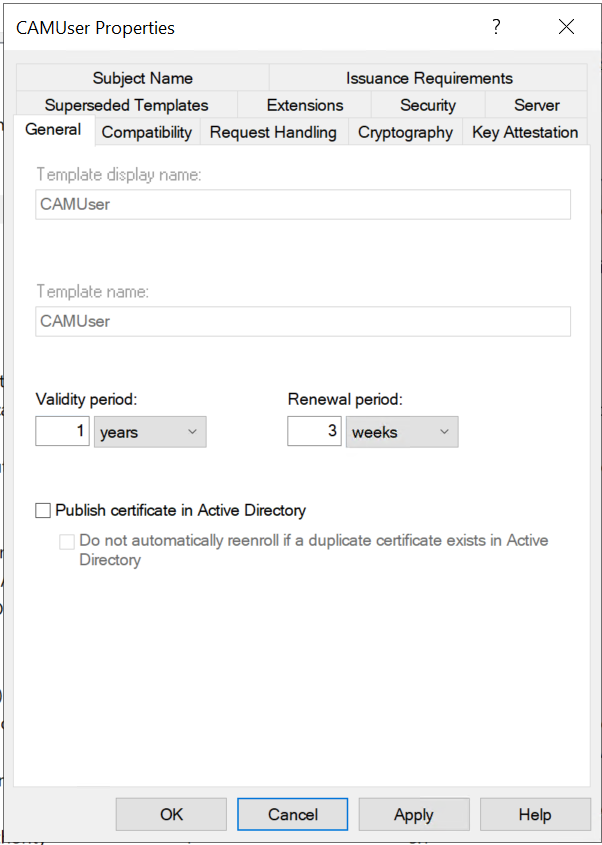
Note: For Key Recovery Agent Certificate templates, only change the template name, then click Apply, then OK. Steps 4 and beyond are not needed for KRA Certificates. -
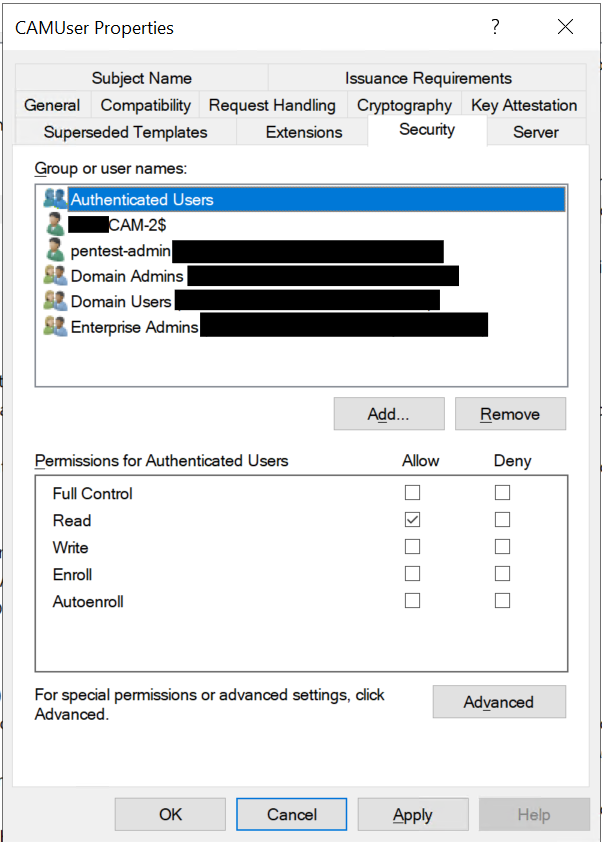
Go to the Security tab. Add and remove security principles here and assign permissions according to your requirements. Refer to the security section of the table at the top of this article. Note: The Certificate Automation Manager server should always have Read permissions.
-
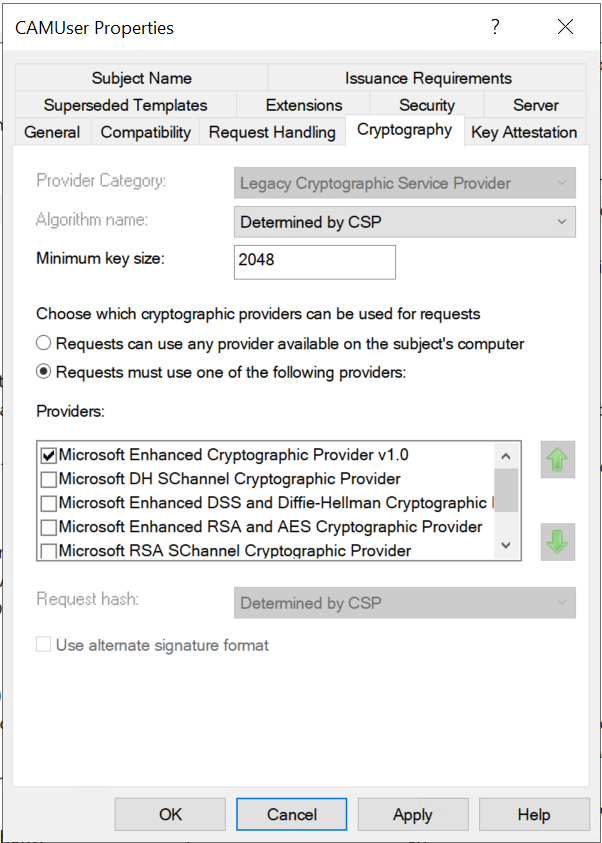
Go to the Cryptography tab. The Algorithm name should be set to Determined by CSP, and the Minimum key size should be set to 2048. GCC will reject Certificates with a lower key size.
-
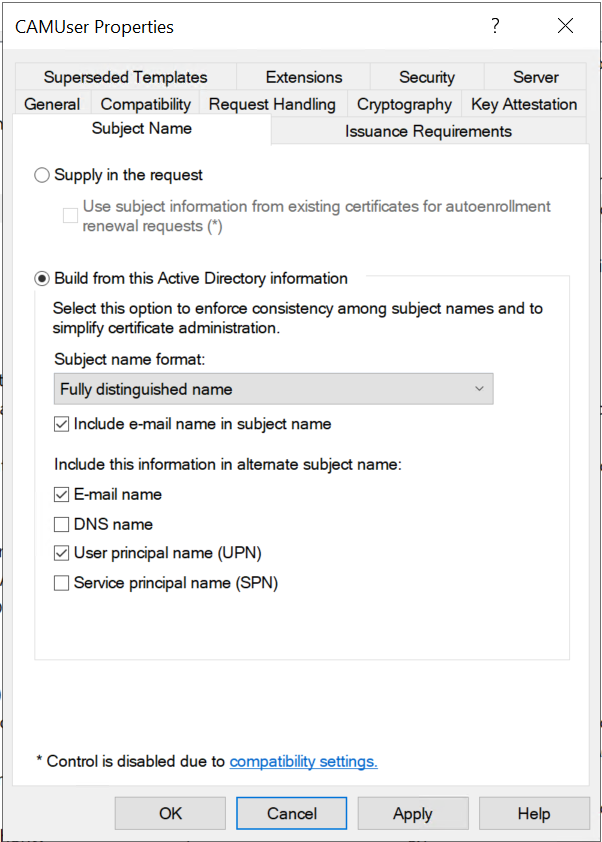
Go to the Subject Name tab. Make sure Build from this Active Directory information is selected. For the remaining fields and options, refer to the information in Common Certificate Template Settings for your configuration.
-
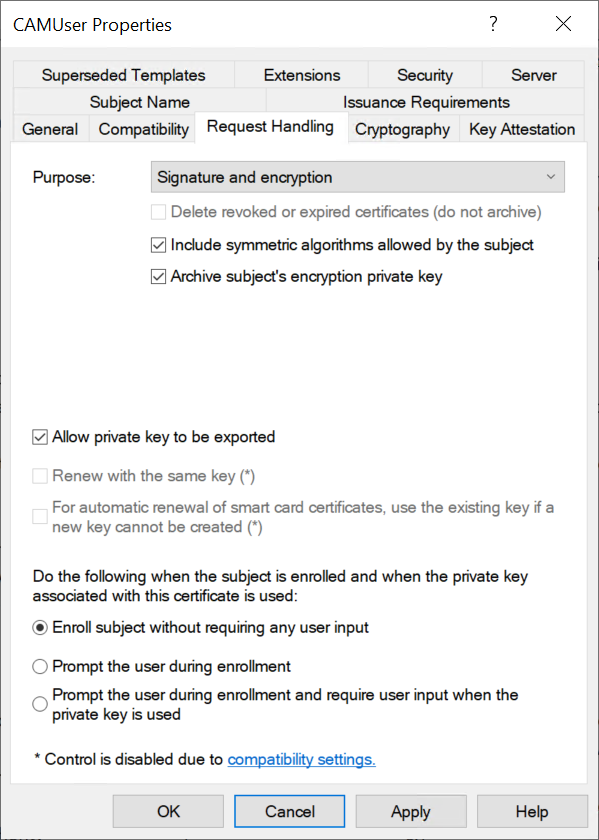
Go to the Request Handling tab. For the remaining fields and options, refer to the information in Common Certificate Template Settings for your configuration.
-
Check all of your settings, make sure everything is correct. Click Apply, then OK.
Related Articles
SSL Configuration Test
Check your certificate installation for SSL issues and vulnerabilities.
