GCC EPKI API Update to accommodate Security Identifier (SID)
Sep 30, 2025
GCC EPKI API Update to accommodate Security Identifier (SID)
To address a certificate-based authentication vulnerability in domain controllers, Microsoft has published a requirement change to support security identifiers on Certificates for authentication purposes.
What is Security Identifier (SID)?
A Security Identifier (SID) is a unique identification number that a computer or domain controller uses to identify a user. It can be generated by using the command 'whoami /user' from a Windows computer." Then include a screenshot similar to this:
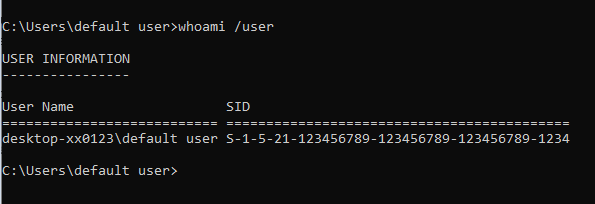
GCC EPKI API will be updated to accommodate the SID (Security Identifier) parameter for a user to provide a value by July 31, 2023. This parameter will be optional until the effective date of November 14, 2023.
IMPORTANT: New EPKI API documentation is available here: https://www.globalsign.com/en/repository/GlobalSign-EPKI-API-User-Guide-v3.0.43d.pdf
SID parameter will be added to the following API commands:
OrderPkcs7 (OrderAndIssueCertificate) Request
(
(
(
(
(
(
(
OrderPkcs12 Request
(
(
(
(
(
(
(
OrderCertificate Request
(
(
(
(
(
(
SSL Configuration Test
Check your certificate installation for SSL issues and vulnerabilities.
