CAA Checking for SSL Certificates
Dec 11, 2025
CAA Checking for SSL Certificates
|
OVERVIEW: This page covers CAA checking for SSL Certificates overview and recommended solutions for common errors. At the completion of this procedure, you will be able to know more about CAA checking for your SSL Certificates and troubleshoot common errors. For more domain management guides, please refer to this page. |
What is CAA Checking?
CAA (Certificate Authority Authorization) Checking enables domain owners to control or restrict which CAs can issue certificates for a particular domain name. By configuring the DNS CAA record, domain owners can limit which Certification Authorities are authorized to issue certificates to that domain name. All CAs that issue publicly trusted TLS certificates are required to check DNS for CAA records prior to issuance.
How does it work?
Domain owners that want to limit issuance to certain CAs can create DNS CAA records that list the CAs they permit to issue certificates to the domain. If a domain has a DNS CAA record, only the CAs listed in the record(s) are allowed to issue certificates for that domain. If no DNS CAA record is present, any CA is allowed to issue certificates for that domain name.
CAs must validate each SAN in the certificate just prior to issuance. The process starts with the FQDN in the certificate e.g., www.eu.example.com, and then works the way up the hierarchy, (to eu.example.com and then to example.com for this domain), looking for CAA records. As soon as a DNS CAA record is found, the CAA records for that domain are processed and the CAA checking ends. Customers can restrict at the higher domain level, example.com, or at lower levels as needed, eu.excample.com.
If the CA encounters a domain that has a CNAME record, the CA will follow that and look for CAA records there.
GlobalSign processes the issue and issuewild tags.
Detailed CAA Processing Logic
For each DNS Name SAN in the certificates request we perform the following:
-
Look for CAA records using the SAN in the request
-
If the lookup finds a CNAME record, we follow that and process the CAA records per the logic below. We will follow up to 10 CNAMEs before ending in an error.
-
If there are no errors and no CAA records with issue tags were returned during the CNAME chasing, we prune the left most node and proceed using that value.
-
We continue doing this until we are down to the Base Domain
Error scenarios that block issuance:
-
If the zone is DNSSEC signed and we encounter a timeout, SERVFAIL or refused error
-
If we get SERVFAIL or refused while trying to determine if the zone is DNSSEC signed
-
If the DNS response is truncated because of too many CAA records, and we haven’t found “globalsign.com” in the CAA issue records, we return a "truncated DNS response" error message
Errors that we conditionally permit issuance:
-
If the zone is not DNSSEC signed, we will permit issuance even if we encounter a timeout or SERVFAIL error
We may cache CAA records for up to an hour, so ever after they are updated it may take an hour for our system to obtain updated records.
Wildcard SANs
Customers may wish to restrict the issuance of wildcard SANs differently than other SANs. When the issue tag is used, that will restrict issuance of all SAN types, but if there is a desire to restrict wildcard SANs differently, then the issuewild tag should be used.
When validating a wildcard SAN, the process starts the same as any other SAN. For example, if the SAN is *.eu.example.com the check will start with eu.example.com. If an issue tag is found for globalsign.com (and there are no issuewild tags), the CAA check will end successfully. If there is an issue tag for globalsign.com and an issuewild tag for one or more CAs other than GlobalSign, then the CAA check will fail.
How to create CAA records
There are various different ways to modify your DNS CAA records. Please refer to the following guides below:
|
IMPORTANT: If you have any issues or questions about whether CAA is supported with your setup, contact your DNS manager for further details. |
Your DNS CAA record should contain "globalsign.com" as shown below.
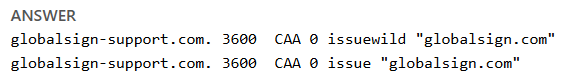
Making your DNS publicly available
Our CAA validation process requires that we find the presence of a DNS entry for the FQDN or in the path up to the Base Domain . We understand under certain circumstances that security or policy prohibits making your A, AA, and MX records public and only enabling them to support the currently annual domain validation (which will being reduced to as little as 47 days in the coming years). At a minimum, we must be able to determine if the DNS zone is DNSSEC signed or not.
If you are unable to make your DNS records public to support frequent issuance, we recommend using a split-horizon approach where internal and external network accesses the same domain name with different IP addresses. It’s also possible to provide different values depending on the source IP address. There are numerous articles on split horizon, also referred to as split-view or split-brain, that can guide you towards an approach that balances your security needs with the ability to provide a DNS entry for your domain for successful CAA validation.
Common Errors
| Error Message |
Reason |
Recommended Solution |
|---|---|---|
|
content of the form: "example.com.": "issue"="another-ca.com" |
The system has detected that the DNS records for the domain (or a parent domain) contain CAA records allowing issuance for “another-ca.com” but not “globalsign.com”. Notice that the domain "example.com." in this error message is where the CAA offending CAA record was found and may be the domain provided in the SAN or a parent domain. |
Remove all CAA records or create a new CAA record permitting "globalsign.com" to issue, then try approving the order again. Please note that this may take up to an hour for the DNS record to propagate. |
| SERVFAIL |
A SERVFAIL response would be returned in one of two cases:
|
In the event of a SERVFAIL response, we would recommend that the customer perform some manual testing to see if they get a SERVFAIL directly from their server when doing a lookup against it, and/or use a propagation tool like DNS Checker - DNS Check Propagation Tool to see if the server is generally available globally. Please make sure that there are no IP address restrictions for accessing DNS records. SERVFAIL errors can be transient (e.g. due to a temporary routing issue somewhere between GlobalSign and the customer's DNS server, or a service restart or similar). If there are no problems found, please try again. |
|
The quorum requirements were not met |
CAs check the values from geographically separated areas around the globe to protect against local DNS hijacking attacks as part of the CA/Browser Forum requirements to support. In this case enough remote nodes did not agree with our primary node, so CAA failed. |
In some cases, customers place geographical restrictions on access to their DNS records. Starting in 2025 CAs are required to check DNS values from multiple geographically separated regions around the world as part of the CA/Browser Forum Multi-Perspective Issuance Corroboration (MPIC) requirement, so customers may need to open up access globally. Please try to issue again as it’s possible that the DNS records have not propagated globally. We will be accessing DNS from the following regions, and this list may be updated from time to time:
|
|
i/o timeout (non-responsive) |
The timeout error implies that your nameservers are down or unreachable. |
If you are presented with this error message, please make sure that your nameservers are up and running and externally reachable. Please contact your DNS provider to verify what caused the failed response from the DNS server, and work with them to resolve the issue. In case there's a firewall in place, please make sure that all IP addresses are allowed access to your DNS records. When your DNS server is properly set up, you can try again to verify your order. Please note that CAA check responses are cached for a maximum of one (1) hour. |
Related Articles
SSL Configuration Test
Check your certificate installation for SSL issues and vulnerabilities.
