Download and Install Code Signing on Rutoken
Dec 17, 2025
Download and Install Code Signing on Rutoken
|
OVERVIEW: This page walks you through the process of downloading and installing the Code Signing and EV Code Signing Certificate on Rutoken 3.0. At the completion of this procedure, your Certificate will be ready to place signatures on drivers, executables, and other files. Learn more about Code Signing Certificate management and other frequently asked questions here. |
On this page
Download and Install Certificate using Fortify
|
IMPORTANT: Rutoken does not support Internet Explorer (IE) Compatibility Mode as installation method. If you selected the Download using Internet Explorer (IE) Compatibility Mode as key generation method during the ordering process, you need to cancel your current order and reorder to change your selection. For bug and hardware related issues, please contact Rutoken manufacturer directly. |
Prerequisites
-
Approved and vetted GlobalSign Code Signing Certificate.
-
GlobalSign-provided eToken.
-
Downloaded and installed Fortify App in your operating system. Ensure that you meet the following system requirements:
• Browsers supported by Fortify: Microsoft Edge, Safari, Firefox and Chrome
• OS supported by Fortify: MAC OS 10.12 or higher, Windows 7 or higher, and Ubuntu 16.04 or higher -
Downloaded and installed Rutoken drivers.
-
For Certificate pickup, you must have access to a Windows PC to proceed. Once the Certificate is installed and stored in the removable device, you may sign from other platforms such as OS X.
Guidelines
- Open the Certificate Download Ready email and launch the pickup link using any browser.
- Enter the Temporary Pickup Password that was set at the time of ordering and click Next to continue.
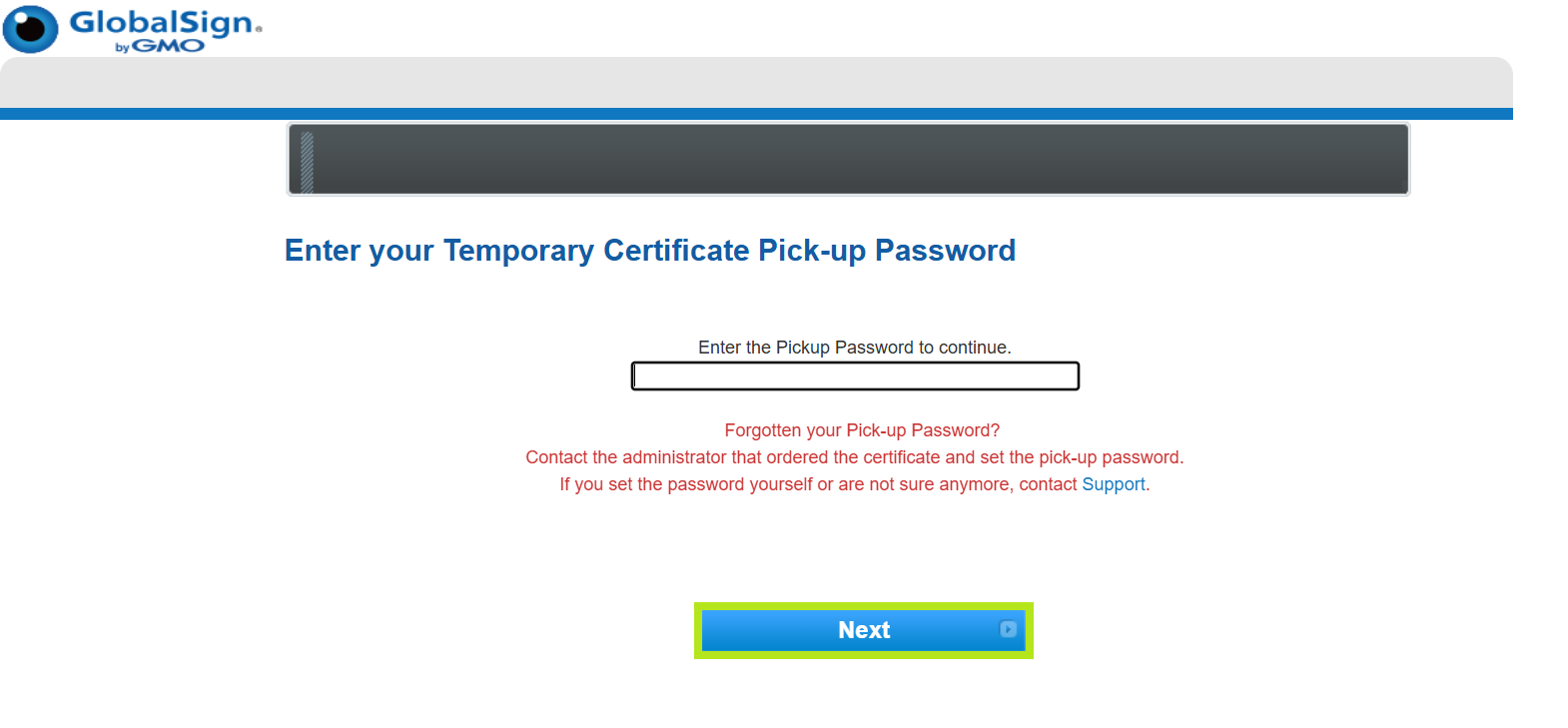
- Tick I agree to the terms above box, then click Next.
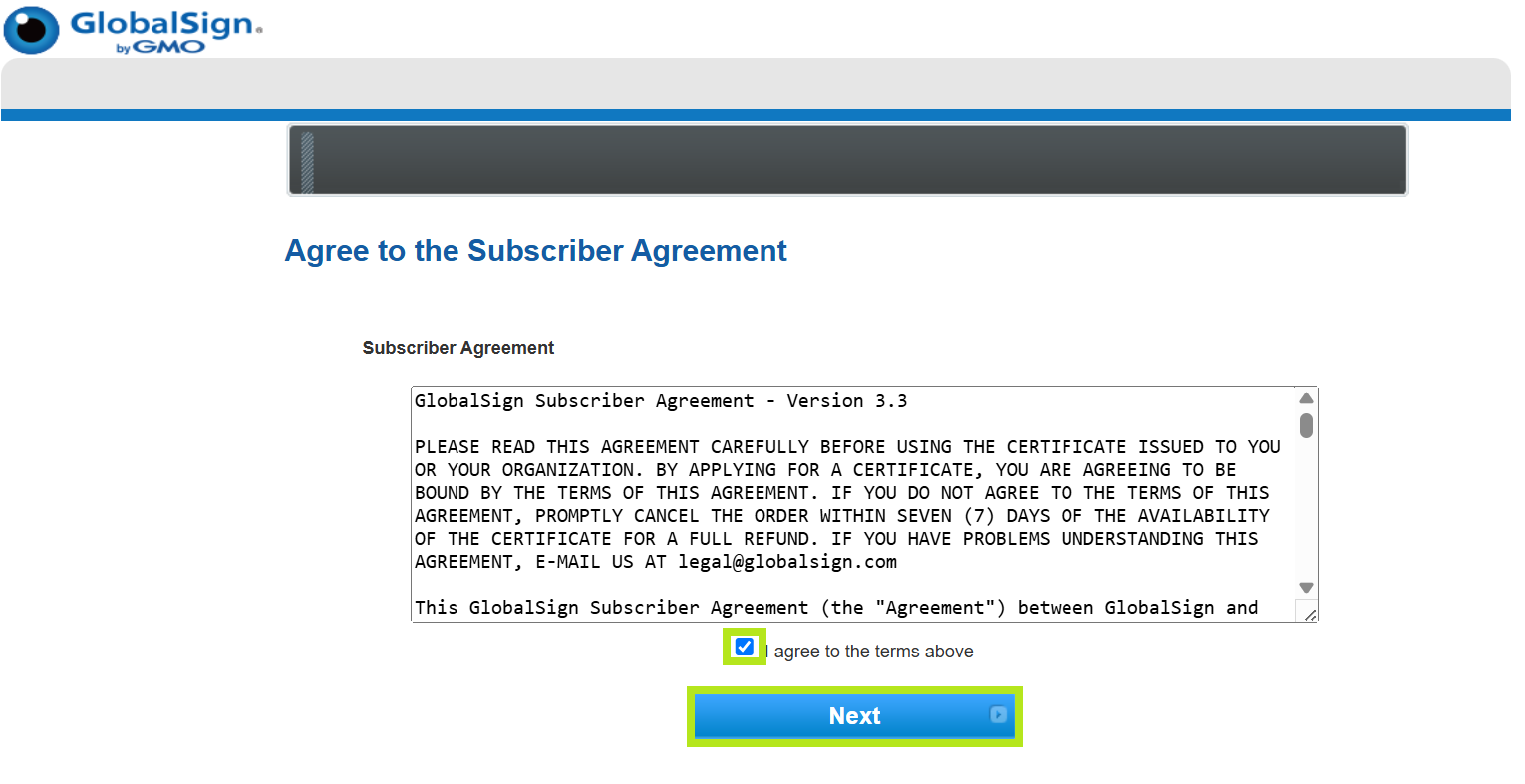
-
A pop-up window for the authorization of code will appear on the Access Permission and on Fortify Authorization. If the both codes matched, click Approve to continue.
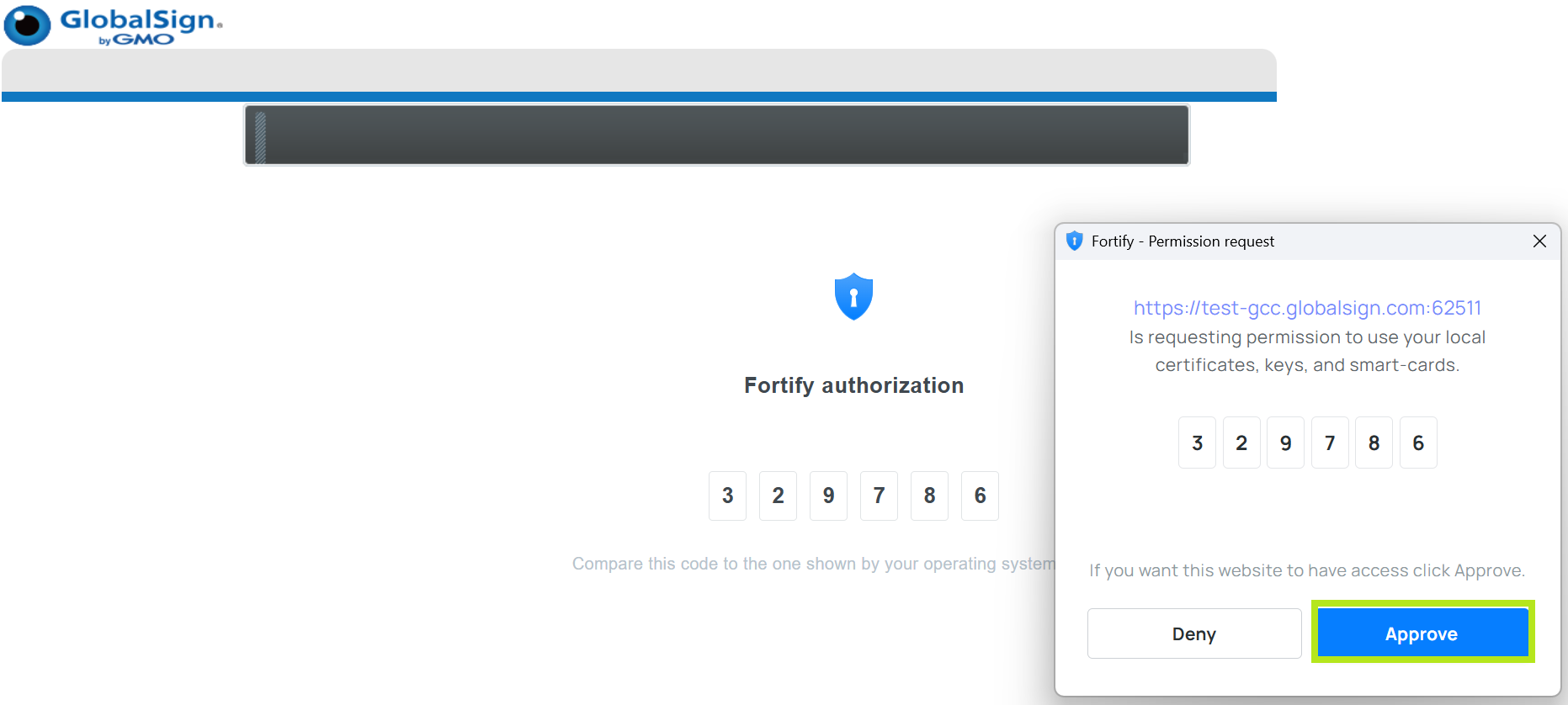
-
In the Create Certificate Request or Self-Signed Certificate window, review the DN or Certificate Identity Detail Information. Then, click Create to continue. Note: If you haven't yet, make sure that your eToken is plugged in to your computer at this point.
-
A pop-up window will appear, then enter the token password. Note: Please wait for a while as it will take a few seconds to process.
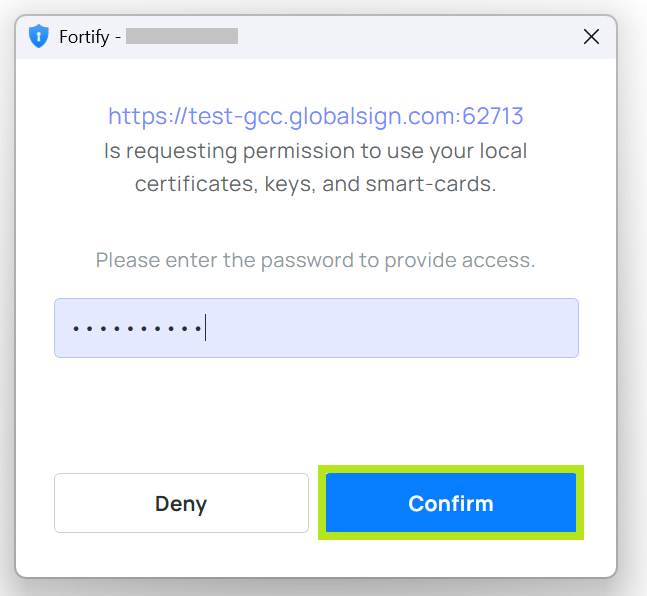
-
On the Install Certificate window, under Select Provider, select Rutoken. Then, click Start to proceed.
- Once Certificate is successfully installed on the token (or local certificate store), a pop-up confirmation window will appear. Click on OK.
Code Signing on Rutoken
Prerequisites
-
Downloaded and installed GlobalSign Code Signing Certificate
-
SHA-256 orders may additionally require GlobalSign Code Signing Root R45 (R3 cross).
IMPORTANT: The Code Signing Root R45 (R3 cross) will need to be installed on the signing computer but not specified as an additional certificate during the signing procedure.
Important SignTool Options
- /ac - Specify an Additional Certificate.
- /a - Automatically selects the best certificate to sign the file from your Windows Certificate Store.
- /n "Certificate Common Name" Specifies the certificate to sign the file from your Windows Certificate Store using the certificate common name.
- /fd SHA256 - Specify the file digest algorithm used in creating file signatures.
- /t - Specify a Microsoft Authenticode-compatible time stamp server.
- /tr - Specify an RFC 3161 compliant trusted time stamp server. *Recommended*
- /td SHA256 - Must be called after "/tr", this command specifies the TimeStamp digest algorithm. *Recommended*}
TimeStamp URLs: SHA-2 based: http://timestamp.globalsign.com/tsa/r6advanced1
|
INFORMATION: Timestamping your Code is extremely important and is highly recommended for every piece of code that you sign. This timestamp will allow the file that you sign to remain valid long after the certificate itself has expired. |
Rutoken version 4.17.0.0 and above
-
You can either sign files out of a working directory or you can place them in your Windows SDK\bin folder.
-
Open the Command Prompt: Windows 7: Start > Run > cmd, or for Windows 8 - 10, press the Windows Key, then type cmd and press enter.
-
Navigate to the directory with signtool.exe.
-
Use the following command to sign your file:
signtool sign /a /tr http://timestamp.globalsign.com/tsa/r6advanced1 /td SHA256 /fd SHA256 c:/path/to/your/file.exe -
Enter your Token Password. If the signing is successful, you will see a prompt informing you so.
-
To verify the successful signature, use the following commands:
Authenticode: signtool verify /v /pa
Kernel Driver Signing: signtool verify /v /kp
You may also verify the signature within the properties of the file, under the Digital Signatures tab.
Rutoken version 4.17.0.0 and below
-
Install the latest java. (jdk and jre). Note: It’s required for keytool and signing a file.
-
Search where the file is located: "rtPKCS11ECP.dll", f.i.. C:\Windows\System32\rtPKCS11ECP.dll
Note: You can get it from the SDK website: https://www.rutoken.ru/developers/sdk -
Download the latest release of jsign from this link and add the file to the library (java jdk bin folder).
-
Create a file called "eToken.cfg". Add the path to the library and the number of the slot into which the token is connected (if there is one on the machine, then most likely on the zero slot), as shown below, and add the file to the library (java jdk bin folder):
name = OpenSC-PKCS11
description = SunPKCS11 via OpenSC
library = C:\Windows\System32\rtPKCS11ECP.dll
slotListIndex = 0 -
Run CMD (Command Prompt) as Administrator and specify the path to the Java jdk bin folder.
-
Get a list of Certificates on your token by using this command:
keytool -list -v -keystore NONE -storetype PKCS11 -storepass 12345678 -providerClass sun.security.pkcs11.SunPKCS11 -providerArg eToken.cfg
Whereas, "-storepass 12345678" is the password for your token. - You need a certificate field: "Alias name" (f.i.., Alias name: RSA)
-
Sign the file "File.exe":
java -jar jsign-5.0.jar --keystore eToken.cfg --alias "RSA" --storetype PKCS11 --storepass 12345678 --alg SHA-256 --tsaurl
http://timestamp.globalsign.com/tsa/r6advanced1 --tsmode RFC3161 File.exe
Related Articles
SSL Configuration Test
Check your certificate installation for SSL issues and vulnerabilities.
